To Share, or Not to Share, that is the Trust Question

Dynamic Digital Age
Technology changes the world at an ever-increasing pace. Whether we like it or not. The change is expedited by both non-digital global occurrences such as the ongoing Covid-19 pandemic (Covid-19) as well as by increased and ever-converging technical capabilities such as connected devices, platforms, available data, artificial intelligence and the like. These enable connecting, inter-connecting and hyper-connecting billions of individuals, organizations, communities, societies and data, with tens of billions of objects and entities. Furthermore, digital has become a must-have, for people, society and our ecosystems, within the European Union as well as globally.
Threats
However smart and otherwise advanced one may want to market this Digital Age is, it is for sure not immune to evil, stupidity, build-fast-fix later business models and other breaches of norms and values. These threaten systems, services, lives of people, key networks and even entire nations, democracies, and societies. And, the true malicious actor does not work alone. They have joined forces, and they win.
The Blame Game
One may feel the urge to blame it all on the others. Or feel the urge to believe that the battle – and the war – is lost. However, there is no way one can point to the other, and blame them for everything. Whatever and whoever is part of the Digital Age is part of the problem. So, that includes you and me.
However, whatever and whoever is part of this, is part of the solution as well. One of the solutions is to join forces, to partner up, to start and continue collaborating, orchestrating our knowledge, values and other capabilities – and to organise ourselves in and for this dynamic Digital Age –. Without being part of those efforts, one will remain just part of the problem, helping to increase it day-by-day. Let’s stop pointing fingers. We are all accountable, and co-accountable.
To Share, or Not to Share
One way to contribute and do one’s part is to share. Share information, share threat intelligence, share good practices, share lessons-learned, and share other knowledge. It should not be that hard to do, right?
What, Why, How and When to Share, to Whom? And, Who am I?
Sharing any information with another has proven not to be an easy feat. These and other queries and considerations for sure come up, even before actually sharing any information to anyone:
- Who am I? Who am I representing here? What is my mandate?
- Why do I feel the urgency or other need to consider sharing that information? Or am I obliged to share, based on new or existing regulations or industry standard practices?
- What do I share, and what not? And, what is the provenance, quality and relevance of the information that could be shared?
- To what extent am I allowed to share it? And to whom?
- Do I know the other party, or not?
- What will the recipient do with it? What is in it for me?
- And, what is the risk? What if something is wrong or goes wrong with the information, with the sharing, with the use?
- Do the potential, envisioned efforts and benefits outweigh the potential risks and consequences?
- Why not just leave it, not engage, and not share information?
Trust is not a Five-Letter Word
These and other considerations all boil down to five letters: trust. Trust and related trustworthiness are always the main enablers, also in any of the cybersecurity domains, any community and any information sharing. Does one have the appropriate level of trust in the assets, trust in its own competences, trust in the organisations and community involved, trust in the technical systems and trust in the ecosystem at large? The right level of trust both brings the courage, confidence and comfort to engage, and share.
Organising Teamwork
One needs many different stakeholders in a community to come to sufficient levels of engagement in order to come to sufficient amounts of relevant and interesting threat intelligence.
Also, although the Digital Age – including cybersecurity and information sharing – are becoming increasingly regulated, those regulations generally only give a trust anchor on the Why, but do not give guidance on the How. Member states that are obliged to organise the How are generally also still struggling with the questions raised above. Society, industry, economy and any sector can not wait. We need to team up, lead the way, lead, share, learn, and continuously improve.
The Dynamics of Cybersecurity Threat Intelligence
The dynamics of cybersecurity, threat intelligence, clearing houses and their various cybersecurity communities are to an already impressive extent captured, orchestrated and deployed by means of the CONCORDIA Platform for Threat Intelligence, which platform consists of three (3) core actionable components: MISP, Incident Clearinghouse and DdoS-Clearinghouse, as visualised below.
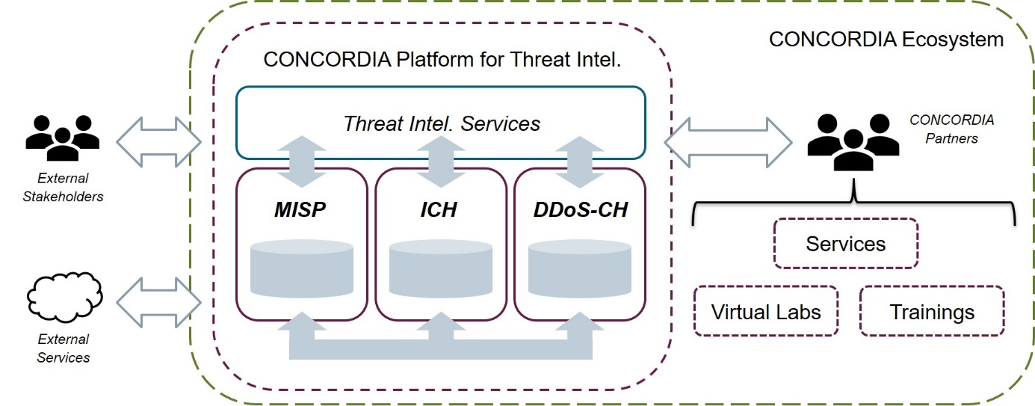
The dynamics of cybersecurity, threat intelligence and its communities – and the impact of both providing threat intelligence as well as knowing about it and using it – augment the fact that one needs to have a high level of trust in the professionals and organisations participating – which do not always know each other –, trust in the threat intelligence and related information and data they share, and trust in what others will do with it.
In brief, the many questions raised above, as well as other considerations need to be arranged for, and been brought into the game of threat intelligence. All this, without making the arrangements difficult to access, read, understand and appreciate, and without the need to having to negotiate, sign and manage bilateral agreements every time.
Trust-Augmenting Instrument, Fit for a Digital Sovereign Europe
Together with representatives of MISP, Incident Clearinghouse and DdoS-Clearinghouse that currently constitutes the CONCORDIA Platform for Threat Intelligence, an instrument has been developed:
- To help answer the questions raised above;
- To make those answer clear and readable;
- To otherwise help augment the information, awareness, adoption, usage and uptake of CONCORDIA Platform for Threat Intelligence, and;
- To arrange for a dynamic framework, that further evolve in this digital Digital Age, and therefore is fit for a digital sovereign Europe, allies and friends.
Trusted Data Sharing, is Sharing based on Trust
Trusted intelligence sharing is sharing intelligence, based on trust. It’s not only about the intelligence or other information – and whether that can be trusted –. No, it start with trust; Am I informed and otherwise comfortable enough and do I therewith have the courage and confidence to become part of this community, and engage?
To bring it from a different perspective:
- Imagine you want to become a member of a sports team, a musical ensemble, an innovation hub, or interest group, to contribute, learn and otherwise engage.
- With that, you want to become part of a certain community, each with its specific habits, codes and rules to set clear expectations of the members of such community as well as protect the interests of both the community and each of the members separately, as well as society and the ecosystem within the community is operating.
- Imagine this is possible regarding sharing of threat intelligence and related trusted data sharing and engagement. Enter, the Dynamic Code of Engagement. A novel trust-augmenting and easy-to-use cybersecurity instrument.
The dynamics of the Digital Age deserve a dynamic framework of principle-based arrangements that are easy to read, understand, become part of and commit to. This, in order to be able to better collaborate, orchestrate and share data based on trust, transparency, appreciation, clear governance and co-accountability.
The Dynamic Code of Engagement will be made available later this year. So, stay tuned.
